Basic introduction
When you use the program for the first time, a registration wizard will pop up, but don’t worry, registration is completely free. If you are not connected to the Internet or do not want to register, you can click the "Later" button at the bottom of the window to experience the magical functions of Cyber Assassin first.
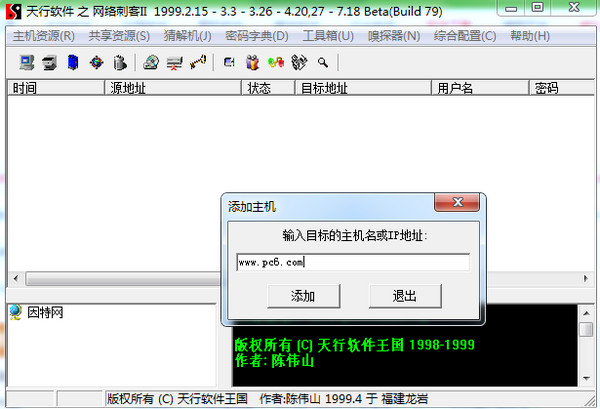
The interface of Cyber Assassin II is as shown in the figure. The author takes Windows 98/2000 LAN as an example to briefly introduce the use of the program. The program runs successfully in Windows 98.
In the Class C LAN we usually use, a host can be identified by its host name and IP address. The IP address is in the form of 192.168.0.X (X ranges from 1 to 255). Hosts with the same IP address cannot appear in the same LAN. , otherwise conflicts will arise.
Function introduction
1. Find the host
Host resources are mainly used to manage shared hosts. When you know the host name or IP address in the same LAN as you, you can add it to your host resources to further realize resource sharing. Select the "Add Host" item in the "Host Resources" menu, enter the corresponding content in the pop-up window, and press the "Add" button. At this point, the corresponding host is added to your resource list. If you don't know the host name and IP address you are looking for, you can use the second menu item "Search Shared Host". Because we are looking for a Class C LAN, you should enter "192.168.0.1" in the starting address. , enter "192.168.0.255" in the end address, and click "Start Search". After a few minutes, the program will complete the search, and all hosts and their shared resources that can be found will be displayed in the small window in the lower left corner. If the information does not change frequently, the user can also save the list so that when the program is started next time, it can be read directly without having to search every time.
2. Shared resources
This function is mainly used to operate shared resources on shared hosts. After finding all the host resources in the LAN, you can use Cyber Assassin II to gain access to the shared resources. Select the corresponding host in the small window in the lower left corner and expand it, right-click the mouse button on the corresponding shared resource, or open the "Shared Resources" menu and select the corresponding option to "map the directory you need to access as a network hard disk". In this way, you can directly open the corresponding directory of the remote computer in "My Computer". If the remote system changes the shared resource settings, you can select "Refresh Shared Resources" to re-read the accessible resources.
When a shared password is set on the local computer, you can select the "Unlock Local Shared Password" menu item to view the read-only password and full access password of the corresponding shared resource. I believe this function will not help you when you forget the password. It's used to restore memory. Of course, if you want to know, you have the right to know.
3. Guessing machine
This is a tool that uses an exhaustive method to try possible passwords to log in to the machine. The password guessing functions that have been implemented include password guessing for POP3 e-mails, FTP file services, and SMB shared resources. Let’s take shared resource guessing as an example to briefly introduce the password guessing method.
Right-click the mouse on the specified shared resource and select "Shared Guessing Machine" in the pop-up menu; or open the "Shared Resources" option in the "Guessing Machine" menu, enter the correct target IP address, and click "Start" Before guessing", you must first set up the correct dictionary, which is the key to success or failure. "Dictionary Settings" includes four tabs. The main tab includes the selection of username and password dictionary files. Here you can define the appropriate password character set and combination method and password length. The remaining three tabs are related auxiliary settings, and users can handle them as appropriate. After the settings are completed, you can also save and read them.
4. Toolbox
Some related network tools are integrated here, including IP <-> host name converter, Finger customer query tool, host port scanning tool, host finder, domain name finder, Telnet client program, etc. You can also use it in the toolbox Check the network status (netstat) and your own IP address. These tools can greatly enhance everyone's understanding of the network.
5. Sniffer
This is Cyber Assassin II's masterpiece, and it might even be the only reason you need to use Cyber Assassin on your LAN. You only need to turn on the "Start Monitoring" option in the "Sniffer" menu. When someone on the local network uses POP3, FTP and Telnet services, for example, someone sends and receives emails through E-Mail client software, or uses services including ICQ, Software such as OICQ has the function of detecting the arrival of new emails. In the main window of the program, the user name, password, time, source address, and destination address are all displayed in clear text and can be seen at a glance. The password for SMB shared resources on the network is given in ciphertext and needs to be set separately. The sniffing results can be saved for later use. However, this feature does not yet support the Windows NT environment.
























![[LTD]Loss tolerance detection](http://softwaredownload4.com/sbdm/img/20240826/66cc6ea4c548d.png?x-image-process=style/style-73)









it works
it works
it works