Things to note:
existmacWhen downloading and installing software, you will generally encounter the following three error situations. Now the editor of Huajun will give you the answer. If you encounter the error, please read it carefully:
1."...The software is corrupted and cannot be opened. You should move it to the Trash"
2."Can't open...software because it comes from an unidentified developer"
3."Can't open...software becauseAppleUnable to check if it contains malware"
When encountering the above three situations, we should:
1. First set:Open any source
2, most software settings can be downloaded and installed normally after opening any source; a small number of softwareiosRestrictions on unsigned application permissions require the execution of command line code to bypass application signature authentication. Therefore it is necessary to:Execute command bypassiosnotarizationGatekeeper.
3. If none of the above operations can solve the problem, then you need to:closureSIPSystem integrity protection.
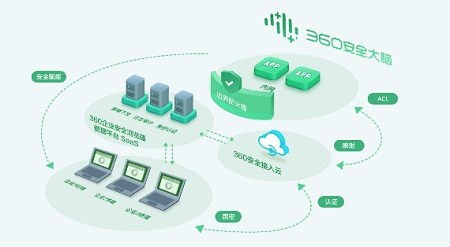
360 Enterprise Security Browser Mac software features
Centralized management solution
The configuration is distributed uniformly by the administrator, so employees no longer face complex configurations
Client + management backend, centralized management improves overall efficiency
Professional people do professional things, and unified services are provided
Flexible and rich configuration strategies, implementing different compatibility solutions for different websites
Multi-layered system protection
Mining protection, prohibiting the execution of digital currency mining scripts to prevent hardware resources from being exploited
Multi-layer protection of files, drivers, processes, and registry to protect system security
Website cloud security, blocking malicious websites and malicious downloads, without getting caught
Download cloud security, download file security detection, anti-Trojan
Sandbox protection, page sandbox protection to prevent unknown viruses
Isolation protection, web page, code, plug-in, CPU process isolation
Safe behavior management and control plan
Multi-angle protection strategies to reduce the risk of internal data leakage within the enterprise
It is prohibited to copy, print, save as... and other potential data leakage behaviors of the organization
Covering user identity watermarks for sensitive systems to prevent screenshots and photos from leaking secrets
Prohibit file upload operations to prevent data from being leaked through email attachments, network disks, etc.
Prohibit the use of developer mode, prohibit viewing of page source code, and control data leakage in debugging mode
360 Enterprise Security Browser Mac Software Features
Provide multi-dimensional protection strategies to reduce the internal leakage index of the enterprise.
Perfectly prohibits copying and printing. Various plagiarism modes prohibit viewing of source code.
Help enterprises achieve consistent platform compatibility through technical controllability, compatibility, and performance.
Greatly reduce the cost of Web development for governments and enterprises, and help them create the best development ecological environment.
360 Enterprise Security Browser Mac Software Advantages
You can customize relevant strategies according to the actual situation and deploy the page compatibility solution that is most suitable for the enterprise.
While enterprise information construction makes office work more convenient, it also makes it easier for enterprise data to be leaked intentionally or unintentionally.
Provide protection mechanisms for multiple dimensions such as terminal security, communication security, Internet security, behavioral security, and data security.
Opening business-related security policies to administrators for unified management improves the overall security capabilities in office scenarios.
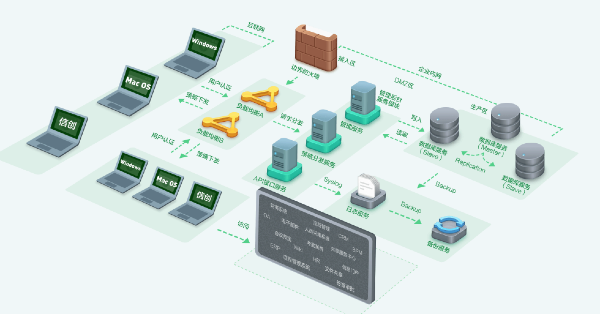
360 Enterprise Security Browser Mac Software Highlights
Help enterprises achieve consistent platform compatibility through technical controllability, compatibility, and performance.
Greatly reduce the cost of Web development for governments and enterprises, and help them create the best development ecological environment.
Provide multi-dimensional protection strategies to reduce the internal leakage index of the enterprise.
Perfectly prohibits copying and printing. Various plagiarism modes prohibit viewing of source code.
Realize the prohibition of file upload to prevent data upload leakage.
Cover watermarks for very sensitive systems to prevent screenshots from leaking.
360 Enterprise Security Browser Mac update log
Developer GG said there are really no bugs this time~
Huajun editor recommends:
The editor of Huajun Software Park recommends that you download the 360 Enterprise Security Browser for Mac. The editor has personally tested it and you can use it with confidence. In addition, Huajun Software Park provides you withwindmill signature,Course opening cloud,Tencent QQ,PCSuite-Mobile Assistant,GreenTurtle Alibaba Cloud IoT AssistantIt’s also a pretty good software, you might as well download it and give it a try if you need it! The editor is waiting for you in wind and rain!




































Your comment needs to be reviewed before it can be displayed