Software description:
Among the vulnerabilities disclosed this time, Meltdown uses the CPU's "out-of-order execution" strategy to steal kernel space information in user space, while Specter uses the CPU's "Speculative Execution" strategy. , which can complete information theft between different users. The impact of the two vulnerabilities is very wide, involving chips from Intel, ARM, AMD and other manufacturers, and the time span is also long, basically covering all models of CPUs after 1995.
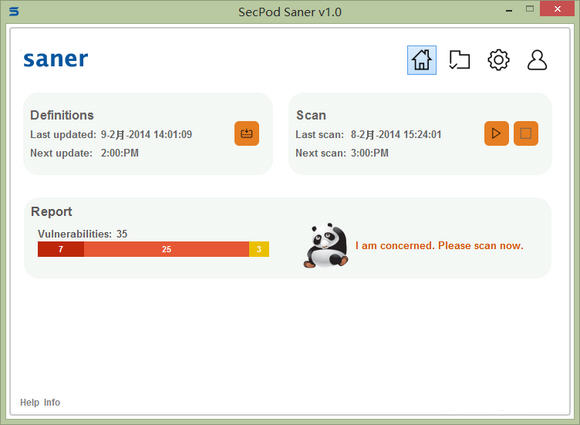
The Hubble Analysis System of Tencent Anti-Virus Laboratory has launched the Meltdown&Spectre detection tool to help users quickly and conveniently complete vulnerability detection, discover hidden dangers in a timely manner, and minimize risks.
This tool does not currently support vulnerability detection on the Windows XP operating system. Tool scan results are for reference only.
How to use:
1. Download Tencent Hubble’s “Meltdown and Specter Vulnerability Detection Tool” to your computer.
2. Use the decompression tool to decompress and run the "MeltdownSpectreScanner.exe" file in the folder.
3. Click the "One-click detection of Meltdown and Specter vulnerabilities" button below, and wait patiently for the scan to complete. This tool will detect whether your computer is affected by two vulnerabilities.
Safety advice:
Currently, the Meltdown vulnerability can be completely repaired through Microsoft patches. If the scan results show "Vulnerable to Meltdown vulnerability", it is recommended to update the patch corresponding to the operating system to protect your computer in a timely manner.
The Specter vulnerability cannot currently be completely repaired solely through Microsoft's patches. If the scan results show "vulnerable to Specter" vulnerability attack, it is recommended to pay attention to official information in a timely manner, update according to the guidelines, and update the CPU firmware in a timely manner. Hardware vendors are already actively developing firmware update patches.
In addition, it is also recommended to pay attention to official update information for installed software, especially browser software updates. At present, many common browsers have released versions that patch vulnerabilities. It is recommended to update to the latest version in time to prevent attacks from the Internet.










































it works
it works
it works