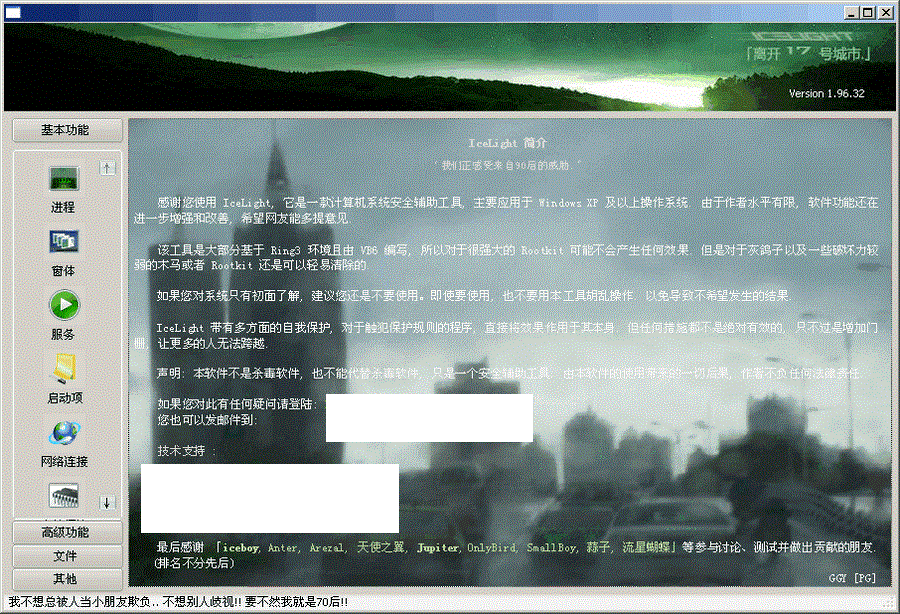
Introduction to IceLight software
It can remove unwanted programs in the computer system through multi-level detection. Its internal functions are very powerful, it can find out Trojan horse backdoors in the system and deal with them in a timely manner. This software can monitor the operation of all programs. The operation of viruses must be licensed by this software. With intelligent analysis and judgment, it can prevent viruses from entering your computer without you knowing it.
IceLight software features
[Process View]
Through more perfect detection methods, running processes can be listed. Terminate the process using the driver.
[Service/Driver Management]
Enumerates all the services/drivers of the system, and the user can judge by himself whether it is a virus startup item, and delete it.
[Image hijacking]
Some Trojans use "IFEO" to prevent security software from running. This software can delete these hijacking items and restore the normal operation of the system.
[Customized virus database]
The virus database of this software is self-defined. The viruses that the software can recognize will increase with the number of viruses you increase. There is no virus database upgrade, and the software will not expire due to the expiration of the virus database.
[Protect system time]
Some Trojan viruses always modify the system, making your anti-virus software expire and lose its protective effect. This software can very well intercept this operation of viruses and Trojans, and intercept prompts when viruses or Trojans modify the system time, causing it to fail to modify the time.
[Registry Protection]
This software monitors the registry operations of the program and immediately prompts and intercepts any suspicious operations.
[View startup items]
This software lists common startup items in the system, so that you can have an understanding of the startup items in the system, make better judgments, and remove viruses.
[IE Repair]
simply list the IE add-ons to help repair IE.
[Kernel module view]
Lists the loaded modules to provide you with useful clues for analyzing the situation.
[SSDT/SSSDT]
Trojans usually use hooks to protect their own processes. This program can restore these hooks and eliminate Trojans.
[Kernel hook scan]
It is said that this is a very abnormal method, and it is quite difficult to restore individual hooks. This program can restore the function that jumped at the beginning.
IceLight software features
1. Complete list of running processes. (A driver is required to terminate the process)
2. List all services and drivers in the system for users to determine whether they are virus startup items and delete them;
3. List IE add-ons and help repair IE;
4. Restore the hooks used by the Trojan to protect its own process, thereby eliminating the Trojan;
5. Restore the function of jumping at the beginning. It is said that this is a very abnormal method;
6. Delete the Trojan hijacking items and restore the normal operation of the system;
7. Customize the virus database and add viruses that can be recognized by the software to the virus database. There is no need to upgrade the virus database and the virus database will not expire;
8. Protect the system time and prevent it from being modified by Trojans;
9. Monitor registry operations in real time, and immediately prompt and intercept suspicious files if found;
10. Monitor the operation of all programs to effectively prevent virus intrusion.
IceLight update log
1.Fix several bugs;
2. Optimize detailed issues;
Huajun editor recommends:
After you use IceLight, I thought you might also wantYouyi U disk encryption software,Kaspersky Total Security,360 safe,Blank And Secure,USB disk encryptorWaiting for software, come to Huajun Software Park to download and use it!






































Your comment needs to be reviewed before it can be displayed