Software introduction:
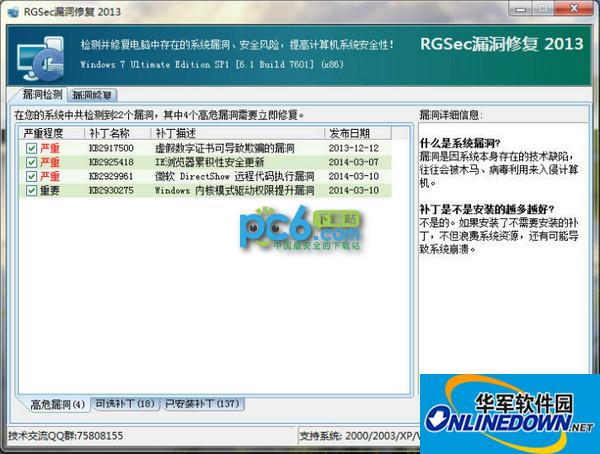
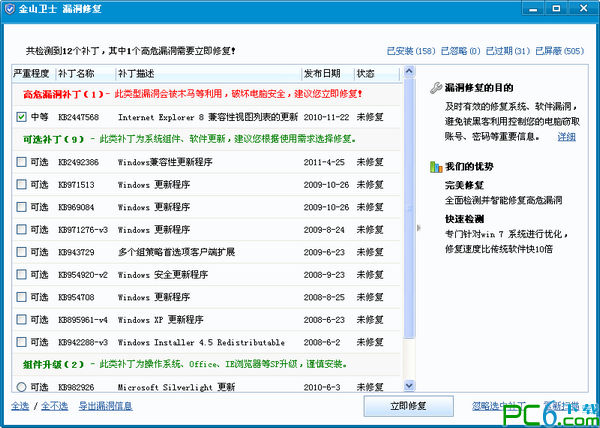
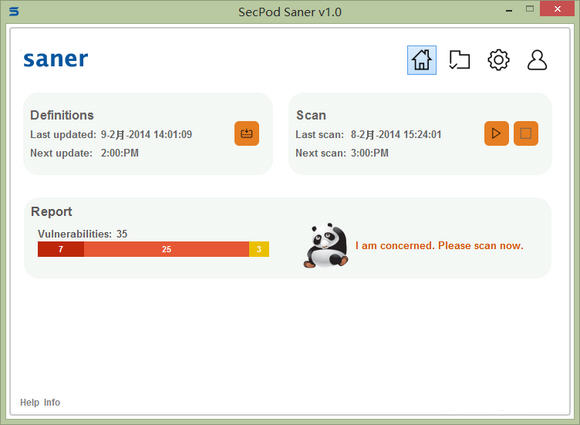
The June 2017 Microsoft patch was released on the 14th. After research and evaluation by 360 security experts, it was confirmed that the following two vulnerabilities require urgent treatment: "Stuxnet III" LNK file remote code execution vulnerability (CVE-2017-8464) and Windows Search remote command execution vulnerability (CVE-2017-8543).
The "Stuxnet III" LNK file remote code execution vulnerability (CVE-2017-8464) can be used to penetrate physically isolated networks.
Microsoft issued a security advisory in the early morning of the 14th, stating that CVE-2017-8464 was used by state-backed cyber attacks to carry out attacks.
It is recommended to immediately use the "Stuxnet III" vulnerability patch repair tool released by the Tianqing team of 360 Enterprise Security Group for detection and repair.
Software description:
What is LNK file remote code execution vulnerability?
This vulnerability has been discovered to be exploited in the wild and has a national background. Hackers can trigger the vulnerability through U disks, CDs, network shares, etc., and completely control the user system. It is extremely lethal to isolation networks such as infrastructure, and the harm is comparable to the previous two generations of Stuxnet attacks.
LNK file remote code execution vulnerability (CVE-2017-8464) This vulnerability is a remote code execution vulnerability that occurs when Microsoft Windows system processes LNK files. When a vulnerable computer is plugged into a USB flash drive containing vulnerable files, the vulnerability attack program can completely control the user's computer system without any additional operations. This vulnerability may also be triggered and exploited by users accessing network shares, downloading from the Internet, copying files, etc.




































Useful
Useful
Useful