Security analysis report:

Features of Web Log Security Analysis Tools
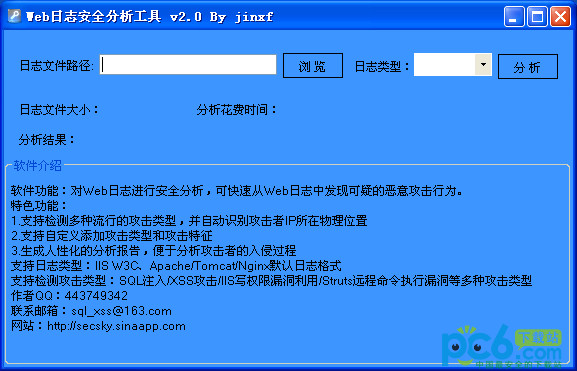
1. Supports detection of multiple popular attack types and automatically identifies the physical location of the attacker's IP
2. Support custom attack signature library, such as adding attack types and attack signatures
3. Generate humanized analysis reports to facilitate analysis of the attacker’s intrusion process. Supported log types:
IIS W3C, Apache/Tomcat/Nginx default log format
Supported detection attack types:
By default, it can detect multiple attack types such as SQL injection/XSS attack/IIS write permission vulnerability exploitation/Struts remote command execution vulnerability. The actual situation depends on the characteristics in the attack signature database.
Feature library description:
The default signature library (AttackRules.ini) defines some common attack signatures and uses regular expression matching; during actual use, users can modify or add attack signatures according to their actual needs.
Environmental description:
This software uses C# language and is developed using VS 2008. Normal operation requires .net framework 3.5 and above.
How to use
Open the program, select the web log file to be analyzed and the corresponding log type, and click the "Analyze" button. After the analysis is completed, a security analysis report is automatically generated.
Related document description:
Web log security analysis tool v2.0.exe: main program
AttackRules.ini: Attack signature library, which defines some common attack signatures. Attack types and attack signatures can be customized in this file.
NewTemplet.tpl: Analysis report generation template.
qqwry.dat: Pure IP database, its function is to automatically identify the physical location of the attacker's IP when an attack log is detected.
































Useful
Useful
Useful