Introduction to Dashizhi computer file leakage prevention system software
Dashizhi Computer File Leak Prevention Software is a powerful and easy-to-operate USB device monitoring and management tool. This software can comprehensively prevent external or internal personnel from intentionally or randomly using USB flash drives, mobile hard drives and other USB flash drive storage devices to copy internal confidential information, causing losses to the unit, and effectively protect the company's business secrets. The editor will talk about it in detail. This software can help enterprises protect the security of computer resources. If you are worried about employees copying company files, you can prohibit copying in this software. You can prohibit employees from copying company files by prohibiting QQ sending and email sending. You can also prevent employees from copying computer data by disabling USB drives from being connected to the computer. The software also provides a variety of prohibition functions, which may result in an operating mode that prohibits copying company data on the software interface, thereby protecting all data on the computer and avoiding the leakage of corporate data.
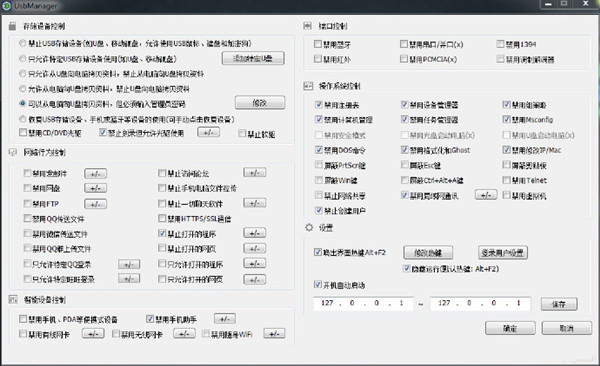
Introduction to the functions of Dashizhi computer file leakage prevention system
a. Comprehensively prevent the leakage of secrets through the Internet
Web page black and white list management. Set a list of URLs that are prohibited from opening, or set a list of URLs that are only allowed to be opened.
It is forbidden to upload files outside the mailbox. It is forbidden to log in to all mailboxes, allowed to log in to specific mailboxes, only allowed to receive emails and prohibited from sending emails, etc.
Chat software is prohibited from leaking secrets. Set specific QQ, allow QQ chat but prohibit file transfer, prohibit QQ group file transfer, prohibit WeChat file transfer, etc.
Program black and white list management. Set a list of programs that are prohibited from running, or set a list of programs that are only allowed to run.
It is forbidden for the network disk to transfer files to the outside world. It is forbidden to use all network disks and cloud disks, and you can also set the use of specific network disks, cloud disks, etc.
It is prohibited to log in to forums, blogs, post bars, spaces, etc., it is prohibited to use ftp to upload files, and it is prohibited to transfer files between mobile phones and computers through the network, etc.
b. Comprehensive monitoring of the use of USB storage devices
Disable the CD/DVD drive and the CD-ROM burning function, but allow the CD-ROM drive to read and disable the floppy drive.
Set a specific USB flash drive, that is, the computer can only recognize the USB flash drive in the white list. At the same time, you can also set secondary permissions for a specific USB disk.
It is forbidden for the computer to connect to all USB storage devices, including USB flash drives, mobile hard drives, mobile phones, tablets, etc. It does not affect USB mice, keyboards, dongles, etc.
Password permission settings. When setting up to copy files from computer to USB flash drive or mobile hard disk, you need to enter the administrator password.
Only allow files to be copied from the USB flash drive to the computer, and prohibit the computer from copying files to the USB flash drive, or only allow the computer to copy files to the USB flash drive, and prohibit the USB flash drive from copying files to the computer.
Monitor USB storage device copy records. Record in detail the log when copying computer files from USB flash drive, including copy time, file name, etc.
c. Operating system underlying protection
Set a global whitelist, prohibit LAN communication, disable virtual machines, prohibit user creation, disable wired network cards, disable wireless network cards, prohibit installation of portable wifi, disable Bluetooth, login password settings, software callout hotkey management, installation directory permission management, uac Management, recovery management
Disable USB disk to start the computer, disable dos command, disable formatting and ghost, prohibit modifying ip/mac, block prtscn, block esc key, block clipboard, prohibit network sharing, prohibit viewing process, block win key, block ctrl+alt+ a key, disable telnet, the system automatically hides and runs when booting
Disable registry, disable device manager, disable group policy, disable computer management, disable task manager, disable msconfig, disable safe mode, disable CD boot, disable infrared, disable serial/parallel port, disable 1394, disable pcmcia, disable modem
It is prohibited to press F8 to enter safe mode when booting, prohibit the optical drive from starting the operating system, prohibit the USB disk from starting the operating system, prohibit the PE disk from starting the computer, etc., to prevent various means from bypassing system monitoring.
Frequently Asked Questions about Dashizhi Computer File Leakage Prevention System
1. What should I do if the shortcut keys cannot call up the software?
There are usually three reasons why the shortcut keys cannot call up the software:
1) The software is not installed successfully, you can try to reinstall it;
2) The software has exited. You can restart the software by restarting the computer and pressing the shortcut key;
3) The shortcut key was pressed incorrectly. Some computers' f-key functions require holding down the fn key.
The shortcut keys generally need to be pressed for 3-5 seconds. If a password is set, the password box will pop up first. The password box is small and can easily be blocked by other windows.
2. What is the default installation path of the software?
Stand-alone version: d:program filesprogramsdzdszusbmonitor
Network version management terminal: d:program filesrealtecksdzbsuprotorserver
Network version client: d:program filesrealtecksdzbsuprotorclient
If there are no special circumstances, try to choose the default installation path.
3. What operating systems are supported? What languages are supported?
Supports all commonly used Windows operating systems, both 32/64 bit.
Mainly in simplified Chinese and English. If you need other languages, you can contact the company for customization.
4. During the installation process, the anti-virus software prompts for a virus?
Software downloaded from the official website of Dashizhi or software issued by Dashizhi sales staff can be installed and used with confidence. If the anti-virus software prompts a virus, this is a false alarm and needs to be added to the whitelist.
5. What should I do if anti-virus software blocks installation?
During the software installation process, if the anti-virus software prompts to intercept information, it must be set to "Allow all operations of the program" and all operations must be allowed, otherwise the software will not be able to be used normally. (It is best to exit the anti-virus software during the installation process)
Dazhi computer file leakage prevention system update log
1.Fix some bugs
2. Optimized some functions
Huajun editor recommends:
Dashizhi Computer File Leakage Prevention System can help you solve many problems. I believe that as long as you dare to use it, you will definitely love it. I also recommend it to you.Kaspersky Total Security,360 safe,Blank And Secure,firewall app blocker,USB disk encryptor






































it works
it works
it works