In 2008, Qihoo 360 launched the free “360 Antivirus” software, forcing the PC security and antivirus market to enter a completely free model. Ruixing, Kingsoft, Jiangmin and even Kaspersky and other long-established anti-virus software manufacturers have all become fish on the chopping block in the face of the strong attack of 360. The market share of personal anti-virus software has dropped again and again, and their glory is no longer. Since then, the overall situation of the domestic PC personal security market has basically been determined.
In 2011, former Rising CTO Liu Gang left with several core technical members who had presided over many important versions of Rising to found Huorong. In September, Huorong Security Laboratory was established. After five years of research and development, on October 18, they launched the 6th version of Tinder Security Software. Adhering to the basic ethics of security manufacturers, Huorong products themselves do not have any infringements such as bundling or privacy collection, and strictly control other types of rogue software. It is very difficult for security manufacturers like Tinder, which neither raises funds nor charges fees, to persist in their independent and pure pursuits. In 2013, the team was so strapped that they couldn't pay wages, so they finally borrowed 1.5 million yuan from friends to tide over the difficulties. But now, everything is slowly developing in Tinder's favor.
The current main business model of Huorong is to provide OEM business of anti-virus engines and security components for enterprise customers. This model allows Huorong to achieve breakeven. In addition, accepting donations is also a source of funding for some independent software vendors.
Software features
Super strong defense to resist account hacking
Adopting active defense mode, it can detect and kill known viruses and Trojans while also defending against unknown security threats.
Lightweight, efficient and enjoyable gaming
Small body and less resources. It does not affect the game efficiency and allows you to play happily.
Filter ads and surf the Internet cleanly
Not only blocks common webpage advertisements, but also filters software pop-up advertisements
Silent protection reduces interruptions
No pop-up prompts unrelated to computer security, no coercion to install unnecessary software
Self-developed engine, domestic high-quality products
Specially in response to domestic security trends, we independently developed a high-performance virus killing engine
Elite team professional protection
Created by former Rising core R&D members with more than ten years of network security experience
How to use
Tinder Secrets-Small functions help you solve big problems
PART1: Tinder Secrets
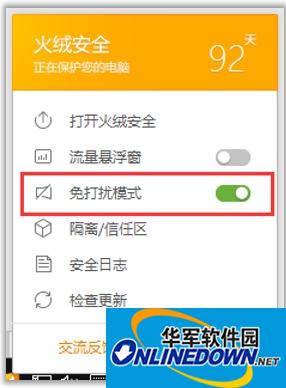
1. Do not disturb mode--game safety
When playing games, you are most afraid of pop-ups, but turning off security software allows viruses to take advantage of them. Just right-click the Tinder Security software tray program and turn on Do Not Disturb mode to kill two birds with one stone.
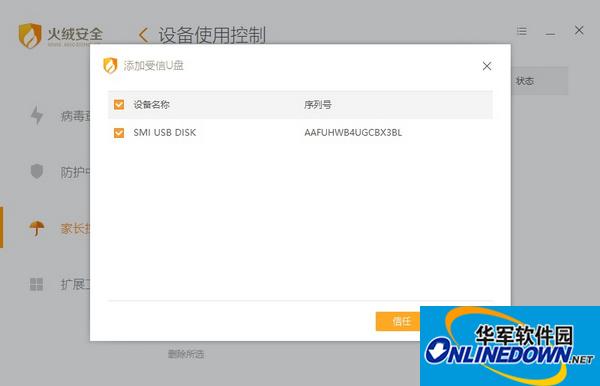
2. Device usage control--all interception of unfamiliar U disks
The misuse of USB flash drives will not only cause viruses to be transmitted through the USB flash drive, but may also leak information inadvertently. Huorong's U disk protection function can detect and defend against U disk viruses, and is enabled by default. At the same time, if the user wants to specify that the USB flash drive can be connected to the computer, he only needs to set up the trusted USB flash drive in Parental Control-Device Usage Control. Tinder security software will help you block unfamiliar USB flash drives from accessing and block threats.
3. Traffic floating window-full monitoring of traffic direction
If you want to monitor the flow direction at any time and understand the program traffic situation, right-click the Tinder Security Software Tray program and open the traffic floating window to monitor the traffic information at any time.
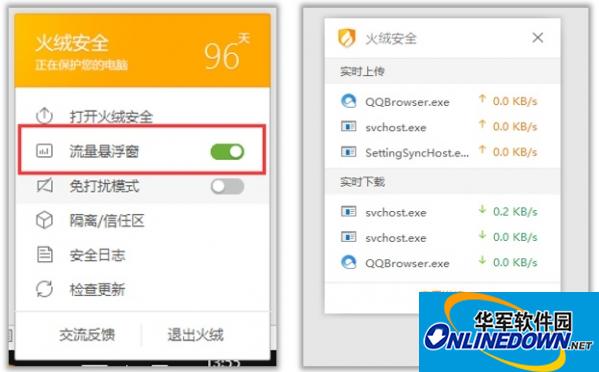
4. Network traffic-network management is not blocked
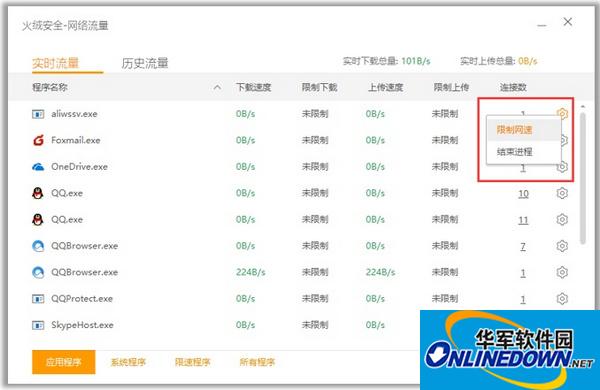
After monitoring through the traffic floating window, you can go to the expansion tool - network traffic function management to better control the Internet access program. Set limit network speed or end the process to prevent network congestion.
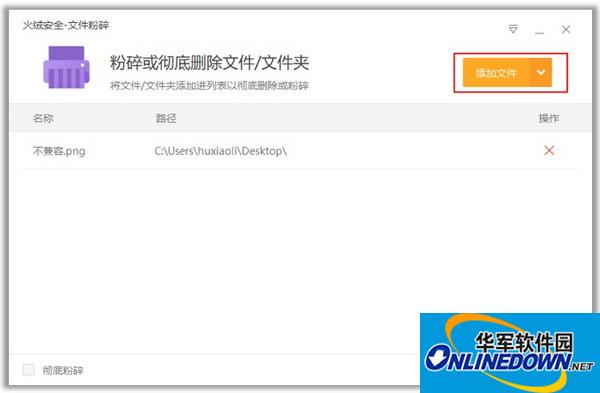
5. File shredding – complete deletion to prevent recovery
During the use of the computer, there are some unnecessary files, but they cannot be deleted through regular deletion. At this time, open the expansion tool - file shredding to completely delete it and prevent it from being restored by technical means, which is stable and safe.
Software dynamics
Tinder Security intercepted the vicious virus Kuzzle: After infecting the computer, it will hijack the browser homepage for profit
According to the Huorong security team, "Kuzzle" has a very high technical level and uses a variety of means to avoid detection by security software. It even steals product digital signatures from well-known security manufacturers and uses the trust mechanism of the security software's "whitelist" to evade detection. Check and kill. What's more serious is that even if the user reinstalls the system, it is difficult to remove the virus, leaving the user's computer under the control of criminal gangs for a long time.
The Huorong security team discovered through technical traceability that “Kuzzle” used a variety of technical means to avoid detection by security software, including stealing the digital signature of the well-known security manufacturer Beixinyuan (300352). When the security software detects the digital signature, it will mistake it for a Beixinyuan (300352) product and automatically let the virus go without scanning or killing it.
“Kuzzle” tamperes with the master boot record (MBR) and volume boot record (VBR) in the computer system. Without repairing the master boot area, users cannot eradicate it even if they reinstall the system.
Kuzzle virus removal and prevention tutorial: http://www.pc6.com/infoview/Article_126548.html
Change log
1 Fixed the BUG that the main interface crashed when opening the main interface and inserting a USB flash drive (Thanks to user zplv587, etc.)
2 Fixed the bug that the quick scan click stops and the estimated time is twice as long as the original one
3 Fixed the bug that when the full scan takes too long, it ends early and the scan time recorded in the log doubles
4 Fixed the problem that when the traffic floating window and the U disk floating window are opened at the same time, the top position of the U disk floating window is invalid (thanks to users CrystallRays, etc.)
5 Fixed the problem that when the U disk has a large number of files, it cannot be ejected during the scanning process.
6 Solved the problem of garbage cleaning-registry cleaning and incomplete application path rules (thanks to user keailvyou, etc.)
7 Fixed the issue where the automatic processing generated by the System process in custom protection would be recognized as "invalid rule"













































it works
it works
it works