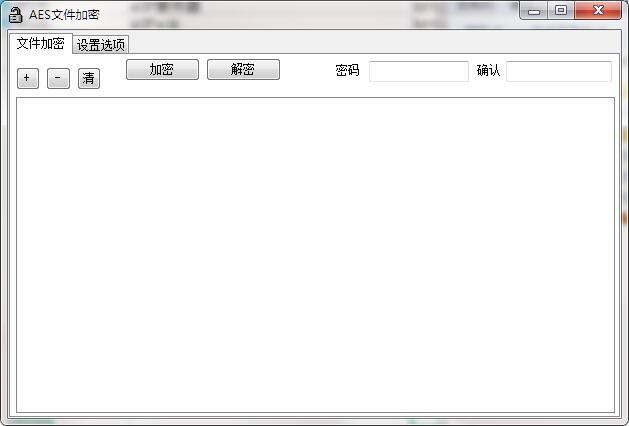
Features of AES encryption tool software
1. Thread optimization for multi-file encryption. But there is no optimization for single files. (Visual inspection of 90 files, 140M, takes 20S, a single file of 880M takes 2M)
2. There is no verification mechanism for passwords. Because it uses a buffered stream operation (encrypting and decrypting 512kb at a time, so even if the password is incorrectly decrypted, it will not waste much time, an exception will be thrown and a prompt box will pop up), and the operation is more convenient.
3. Since the main purpose is not to learn encryption algorithms, I did not delve into it. There is only one algorithm, AES.
4. The label "(encrypted)" in the file name cannot be changed. Otherwise it will be excluded.
AES encryption tool usage instructions
1. Drag and drop files directly into the program’s list control
2. You can check the box in the settings list to delete the original file.
3. No file shredding function
AES encryption tool software instructions
With the development of symmetric cryptography, the DES data encryption standard algorithm has been unable to adapt to the data encryption security requirements of today's distributed open networks due to its small key length (56 bits). Therefore, in 1997, NIST publicly solicited a new data encryption standard, namely AES [1]. After three rounds of screening, the Belgian Joan Daeman and Vincent The Rijndael algorithm submitted by Rijmen was proposed as the final algorithm for AES. This algorithm will become the new data encryption standard in the United States and be widely used in various fields. Although people still have different views on AES, in general, AES, as a new generation of data encryption standard, brings together the advantages of strong security, high performance, high efficiency, ease of use and flexibility. AES is designed with three key lengths: 128, 192, and 256 bits. Relatively speaking, the 128 key of AES is 1021 times stronger than the 56 key of DES [2]. The AES algorithm mainly includes three aspects: round change, number of turns and key expansion. This article takes 128 as an example to introduce the basic principles of the algorithm; combined with AVR assembly language, the advanced data encryption algorithm AES is implemented.
AES is a group key, the algorithm inputs 128 bits of data, and the key length is also 128 bits. Use Nr to represent the number of rounds of encryption for a data packet (the relationship between the number of encryption rounds and the key length is listed in Table 1). Each round requires the participation of an expanded key (i) with the same length as the input packet. Since the length of the externally input encryption key K is limited, a key expansion program (Keyexpansion) is used in the algorithm to expand the external key K into a longer bit string to generate encryption and decryption keys for each round.
1.1 circle change
Each circle transformation in AES consists of the following three layers:
Non-linear layer - perform Subbyte transformation;
Line mixed layer – perform ShiftRow and MixColumn operations;
Perform AddRoundKey operation.
① Subbyte transformation is a non-linear byte transformation that acts on each byte in the state, and can be mapped through the calculated S box.
② ShiftRow is a byte transposition. It cyclically shifts the rows in the state according to different offsets, and this offset is also selected based on Nb[3]
③ In the MixColumn transformation, each column in the state is regarded as the result of multiplying the polynomial a(x) on GF(28) and the fixed polynomial c(x). The coefficient of b(x)=c(x)*a(x) is calculated as follows:
*The operation is not an ordinary multiplication operation, but a special operation, that is, b(x)=c(x)·a(x)(mod x4+1) For this operation b0=02. a0+03. a1+a2+a3 Let xtime(a0)=02. a0
其中,符号“。”表示模一个八次不可约多项式的同余乘法[3]。
For the inverse change, the matrix C needs to be changed to the corresponding D, that is, b(x)=d(x)*a(x).
④ The key addition operation (addround) is to “XOR” the corresponding bytes in the circle key state bit by bit.
⑤ According to the properties of linear change [1], the decryption operation is the inverse change of the encryption change. This will not be described in detail here.
1.2 rounds of changes
For different packet lengths, the corresponding number of round changes is different, as listed in Table 1.
1.3 Key expansion
The AES algorithm uses the external input key K (the number of words in the key string is Nk), and obtains an extended key totaling 4 (Nr+1) words through the key expansion program. It involves the following three modules:
① Position transformation (rotword)-change a 4-byte sequence [A,B,C,D] into [B,C,D,A];
② S-box transformation (subword) - replace a 4-byte S box with an S-box;
③ Transform Rcon[i]——Rcon[i] represents a 32-bit word [xi-1,00,00,00].
x here is (02), such as Rcon[1]=[01000000];Rcon[2]=[02000000];Rcon[3]=[04000000]……
Generation of extended key: The first Nk words of the extended key are the external key K; the following words W[[i]] are equal to the "exclusive OR" of the previous word W[[i-1]] and the previous Nk word W[[i-Nk]], that is, W[[i]]=W[[i-1]]W[[i- Nk]]. But if i is a multiple of Nk, then W[i]=W[i-Nk]Subword(Rotword(W[[i-1]]))Rcon[i/Nk].
AES encryption tool update log
Working day and night just so you can be happier
are all gone!
Huajun editor recommends:
The AES encryption tool is a high-performance software that meets everyone's requirements. The software is free and non-toxic. It has absolutely positive reviews. Our Huajun Software Park has the most authoritative software, which is green and free, officially authorized, and similar.Black Beetle File Encryption Lock,Yitong folder encryption software,Secret folder encryption tool,Universal Encryption Master,U disk super encryption 3000, I hope everyone will come to download it!





































Useful
Useful
Useful