Yikongwang is a simple, easy-to-use, feature-rich LAN computer monitoring software. It focuses on LAN Internet monitoring, desktop screen monitoring, U disk management and control, email management and control, file outgoing control, traffic control, document transparent encryption and other comprehensive functions. All-in-one network monitoring and management software. Occupying very few resources, lightweight design, industry-leading core monitoring technology, easy to operate in one minute, it is an essential network management tool for LAN monitoring and management.
Function introduction
1. Screen monitoring
It can monitor the LAN computer screen in real time, take regular screenshots and photos of the computer screen operations in the LAN, and save the screen history for future audit needs.
Multi-screen monitoring can monitor multiple employee computer screens in real time, and can choose to monitor or control employee screen operations.
2. Web page monitoring
Monitor web browsing behaviors such as web pages, online postings, and online shopping, and also provide web page snapshots to save web page records.
URL blacklist: Access to URLs added to the blacklist can be prohibited.
URL whitelist: Only allow employees to access URLs in the whitelist URL library.
3. Email monitoring
Perfectly monitor outgoing emails from webmail pages and email content and attachments sent and received based on POP3, SMTP, etc.
4. File outgoing monitoring
Completely records various file operations, including creation, access, modification, deletion, copy, etc.;
Record employee document outgoing behavior. Including QQ outgoing, U disk copy outgoing, browser outgoing, etc., the source files sent out can also be recorded.
5. Document outgoing control
Users are prohibited from leaking files through browsers, instant chat tools, USB flash drives, etc.
It is prohibited to copy files to USB devices (U disk, mobile hard disk, etc.), shared directories, and network hard disks.
It is prohibited to copy files from USB devices (U disk, mobile hard disk, etc.), copy files from shared directories, copy files from network hard disks, and limit the size of files copied from USB devices.
6. Software management and control
This LAN monitoring software can be set to view usage information such as startup and shutdown times, window titles, etc. of various software programs;
Software blacklists can prohibit employees from opening software programs that do not comply with regulations;
QQ games, web games, China Game Center, Great Wisdom and other game stock trading software are prohibited.
7. Flow control
This LAN monitoring software can display the network traffic usage of each employee's computer in real time, facilitate management to respond quickly to network abnormalities, ensure normal bandwidth for key services, and make the entire network smoother.
Display the bandwidth of each computer in real time, including upload, download and total traffic;
The upper limit of upload and download for each employee can be set;
8. Print monitoring
Can completely record all printing operation behaviors. While preventing printing leaks, it can also reduce unnecessary printing behaviors and save printing costs.
9. Content filtering
Easy Control King LAN monitoring software can customize keywords to filter web page content, topics, forums, blogs, and Weibo keywords.
10. Chat filtering
You can set employees to only log in to the QQ number specified by the company to prevent employees from using private QQ chat behavior.
11. Violation alarm
Alerts for illegal operations on controlled LAN computers, such as illegal access to web pages, illegal use of chat tools, illegal use of bandwidth traffic, etc.
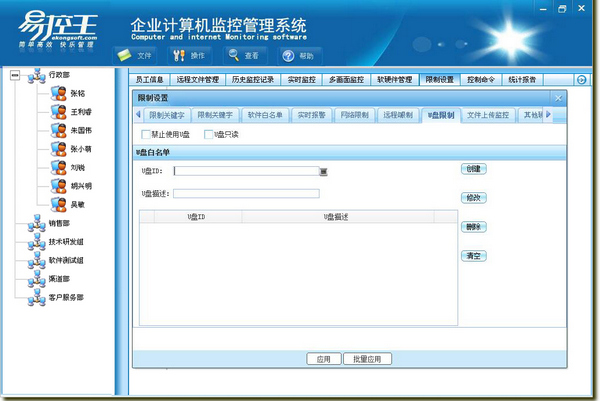
12. Hardware control
Application policies can be set for external devices in LAN employee computers respectively, and the use of hardware such as U disks, mobile hard disks, optical drives, wireless network cards, and 3G network cards can be prohibited to prevent file leakage through hardware devices.
13. Authorized mobile storage devices
The use of mobile storage devices (U disks, mobile hard drives, etc.) on LAN employee computers can be authorized and managed. Unauthorized mobile storage devices are not allowed to be used within the company.
14. Authorize multiple administrators
Different administrators within the LAN can be assigned different management departments. You can also assign different management rights to different administrators.
15. Advanced policy control
It can formulate LAN safe Internet management strategies for different employees in the LAN for different periods of time, such as web page access, email sending and receiving, chat tool use, network posting, etc., and humanely manage various Internet behaviors to make employees' Internet access more effective and safer.
16. System management and control
Remote control: Administrators can remotely operate remote computers in the LAN online through the Easy Control King LAN monitoring software, and remotely shut down, restart, and log off the computer. Remotely uninstall and upgrade clients. Remote execution of commands, etc.
System restriction policy: You can prohibit the client from using the registry, prohibit IE downloads, prohibit modification of IP address, disable task manager, disable adding and removing programs, automatically synchronize server time, prohibit Internet access when disconnected from the server, etc.

Software features
1. Powerful function, one-click operation;
2. The operation is simple, and a computer novice can easily get started in one minute. It is suitable for use by business managers;
3. Efficient and stable. The core engine of the product adopts a self-developed core driver kernel, coupled with efficient and stable excellent algorithms, with powerful functions and stable performance;
4. It occupies very low resources. It is an industry-leading resource optimization module that does not load processes and will not be forced to close. It is more stable than similar software;
3. Pure software architecture, no changes are required to the company’s inherent computers and network equipment;
4. Security and confidentiality. The system adopts multiple high-strength encryption mechanisms. You can set the software login password and access employee password to effectively protect the security of monitoring information.
5. Cross-Internet supervision can simultaneously supervise the computers of employees in local area networks and foreign branches, effectively solving the problems encountered by users such as difficulty in monitoring remote branches.

How to use
Quickly install and get started in just 3 steps!
1: Management side, installed and deployed on the manager’s device.
2: Controlled terminal, installed and deployed on employee computers.
3: Open the management terminal, set the control strategy, view the monitoring records, and use it happily.
Change log
1. Optimize the resources occupied by screen logs and support real-time recording.
2. Optimize the logging module.
3. Fix other minor bugs in the software.