360 Trojan FirewallDownload, this independent version of 360 Trojan Firewall is extracted from the comprehensive functional components of 360 Security Guard. It has three built-in functions: entrance defense, isolation defense and system defense. It can block all software with Trojan behavior from sending information to the network to ensure the information security of your computer. Since this software is a small tool on 360 Security Guard, the editor provides you with the official package download of 360 Security Guard. Let’s try it together.
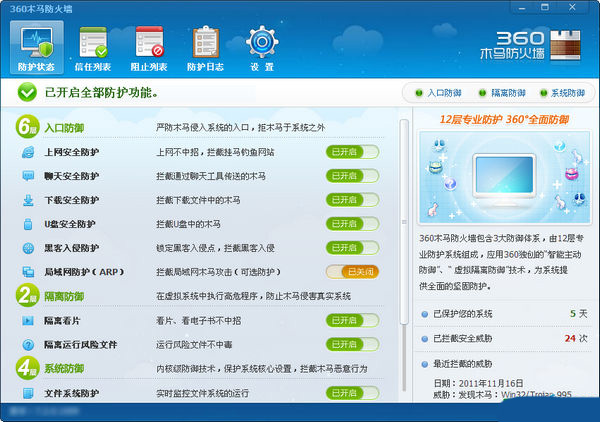
360 Trojan Firewall Features
1. Traditional security software "focuses on checking and killing, but neglects protection". It often checks and kills the Trojan after it sneaks into the computer and steals the account. Even if the Trojan is killed, it will remain, the system settings will be modified, and the various losses suffered by netizens will be irreparable.
2. 360 Trojan Firewall adopts original "billion-level cloud defense" technology. It achieves super protection for users' computers and effective interception of Trojans through real-time protection of key computer locations and intelligent analysis of Trojan behavior, combined with a "cloud security" system composed of 360 million users.
3. In order to effectively prevent the attacks and damage of malignant Trojans such as driver-level Trojans, infected Trojans, and stealth Trojans, 360 Trojan Firewall adopts kernel driver technology and has eight layers of "system protection" including network shield, LAN, U disk, driver, registry, process, file, and vulnerability, which can comprehensively resist Trojan attacks that invade the user's computer through various channels.
4. The well-known domestic security forum Kafan’s test results for 360 Security Guards show that even temporarily unrecognizable Trojan virus samples can be intercepted by the main defense function of 360 “Trojan Firewall”, with an interception score of almost 100%. It can be called the anti-Trojan software with the strongest killing and protection capabilities in the world.
Note: If all protections of 360 Trojan Firewall are not fully enabled (except LAN ARP firewall), the 360 Security Guard icon will have a red exclamation mark. Users only need to turn it on completely and the red mark will disappear.
360 Trojan firewall installation method
1. After downloading 360 Trojan Firewall from this site, use 360 compression software to decompress it. After decompression is completed, double-click the .exe file to enter the software installation interface, check [I read and agree to the agreement], you can click [Install Now] and the software will be installed by default.

2. Or you can click [Custom Installation]. In the window that opens, you can click [Change] to select the installation location of the 360 Trojan Firewall. After completing the selection, click [Install Now].

3. 360 Trojan Firewall is being installed. You need to wait patiently for the software installation to be completed.

How to use 360 Trojan firewall
1. Open the installed 360 Security Guard software and click [Security Protection Center] on the right
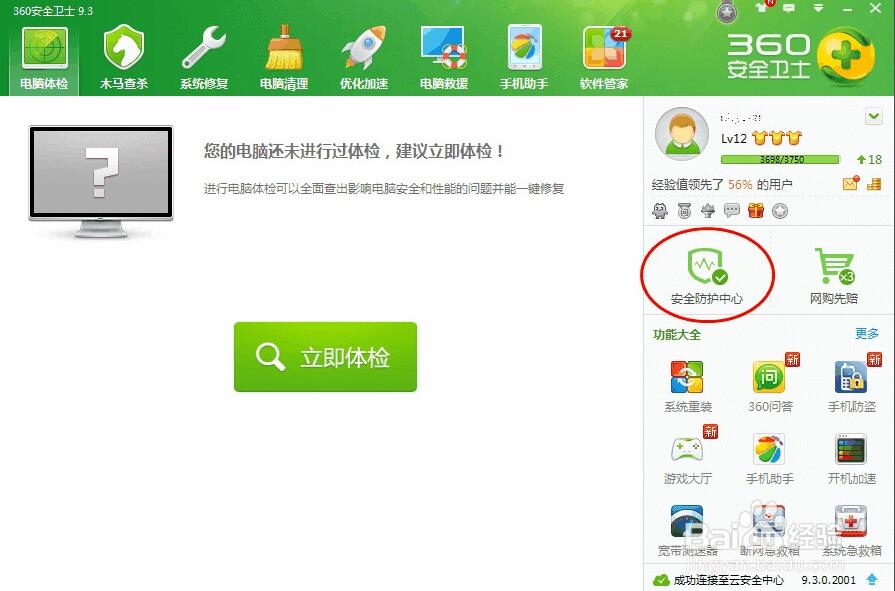
2. The function of entering the Trojan firewall is integrated into the security protection center

3. Click to expand various types of protection; hover the mouse over the turned on protection, and "Close" will be displayed; click "Close" to turn off the corresponding protection.
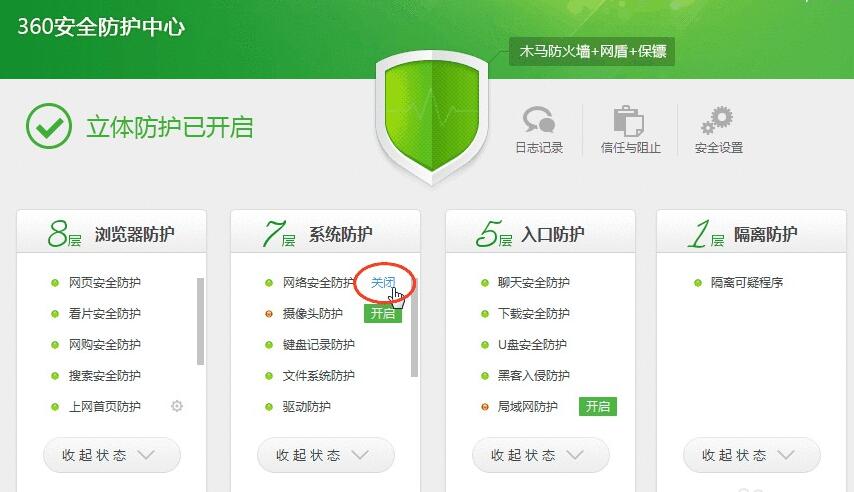
4. Click "Turn on" next to the protection that is not turned on; you can turn on the corresponding protection;

360 Trojan Firewall update log:
1. Fixed other bugs;
2. Optimized software compatibility.
Huajun editor recommends:
360 Trojan Firewall is the world's first firewall dedicated to resisting Trojan intrusions. It applies 360's original "billion-level cloud defense" to protect system security at multiple levels and in all directions, from preventing Trojan intrusions to system defense and killing, from enhancing network protection to reinforcing underlying drivers, combined with advanced "intelligent active defense". If you are interested, you can also download software such as Youyi U disk encryption software, Kaspersky all-round security software, and Cloud Machine Manager.








































