-
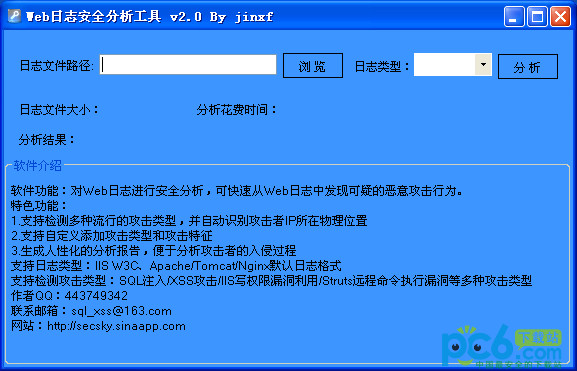
Web log security analysis tool
- Size: 4.8M
- Language: Simplified Chinese
- Category: Anti-black and anti-horse
- System: winall
Version: V2.0 green free version | Update time: 2024-12-30
Similar recommendations
Latest updates
Web Log Security Analysis Tool Review
-
1st floor Huajun netizen 2021-01-17 21:30:46The web log security analysis tool is very useful, thank you! !
-
2nd floor Huajun netizen 2018-04-13 00:45:12The web log security analysis tool interface design is easy to use and has rich functions. I highly recommend it!
-
3rd floor Huajun netizen 2020-11-28 14:00:23Web log security analysis tool software is very easy to use, downloads quickly and is very convenient!
Recommended products
-

360 system first aid kit (64 bits)
-

Windows Trojan Scavenger 2010
-

Trojan Removal Expert 2017
-

Rising Security Assistant
-

360 system first aid kit
-
360 system first aid kit (64 bits)
-

Kingsoft Guard System File Repair Tool
-
Svr virus killing tool
-

marvell yukon 88e8057 network card driver
-

Guardian God·Cloud Check and Kill (specialized in killing web Trojans)
- Diablo game tool collection
- Group purchasing software collection area
- p2p seed search artifact download-P2P seed search artifact special topic
- adobe software encyclopedia - adobe full range of software downloads - adobe software downloads
- Safe Internet Encyclopedia
- Browser PC version download-browser download collection
- Diablo 3 game collection
- Anxin Quote Software
- Which Key Wizard software is better? Key Wizard software collection






















