market
Product classification
-
 Chuangyu Cloud Shadow Host Security Protection SystemChuangyu Cloud Shadow uses behavioral analysis to detect and respond to threats that go undetected by traditional host systems. Rather than using signatures to inspect files and processes, Chuangyu Cloud Shadow uses behavioral analysis algorithms to examine events collected from endpoints across the network, identify malicious behavior, and alert security teams to help them respond to the attack or investigate further. .View now
Chuangyu Cloud Shadow Host Security Protection SystemChuangyu Cloud Shadow uses behavioral analysis to detect and respond to threats that go undetected by traditional host systems. Rather than using signatures to inspect files and processes, Chuangyu Cloud Shadow uses behavioral analysis algorithms to examine events collected from endpoints across the network, identify malicious behavior, and alert security teams to help them respond to the attack or investigate further. .View now -
 IP positioning data offline library (commercial version)The IP positioning data offline database (commercial version) contains all high-precision data in China (excluding Hong Kong and Taiwan), provides all locations where IP appears, provides street-level positioning data, and has a short update cycle.View now
IP positioning data offline library (commercial version)The IP positioning data offline database (commercial version) contains all high-precision data in China (excluding Hong Kong and Taiwan), provides all locations where IP appears, provides street-level positioning data, and has a short update cycle.View now -
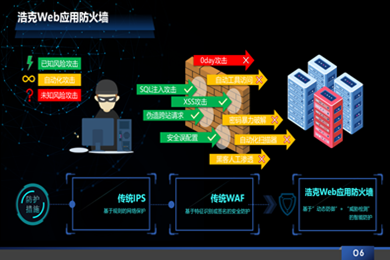 Hulk Web Application FirewallHulk WAF is a web application security protection product that integrates active dynamic defense and conventional static protection. It provides website application-level security protection, anti-tampering, anti-hotlinking, anti-collision library, anti-crawler, anti-automatic scanning, and anti-unknown threats.View now
Hulk Web Application FirewallHulk WAF is a web application security protection product that integrates active dynamic defense and conventional static protection. It provides website application-level security protection, anti-tampering, anti-hotlinking, anti-collision library, anti-crawler, anti-automatic scanning, and anti-unknown threats.View now -
 Data leak prevention systemThe data leakage prevention system includes complete file encryption software functions, various types of data encryption and group encryption software deployment to create an intranet security system and is committed to providing professional information security monitoring, management consulting and technical services to enterprises and institutions.View now
Data leak prevention systemThe data leakage prevention system includes complete file encryption software functions, various types of data encryption and group encryption software deployment to create an intranet security system and is committed to providing professional information security monitoring, management consulting and technical services to enterprises and institutions.View now -
 IoT card patch card industrial IoT card traffic cardWe provide China Mobile IoT cards, either plug-in cards or patch cards, 30M/month, annual package of 360M, 3.9 yuan/card, the price can be negotiated if the quantity is large. If you need other traffic, please contact us by phoneView now
IoT card patch card industrial IoT card traffic cardWe provide China Mobile IoT cards, either plug-in cards or patch cards, 30M/month, annual package of 360M, 3.9 yuan/card, the price can be negotiated if the quantity is large. If you need other traffic, please contact us by phoneView now -
 Penetration testing of operating systems/application systems/Web programs/APP software, etc.The purpose of penetration testing services is to fully explore and expose system weaknesses so that managers understand the threats their systems face.View now
Penetration testing of operating systems/application systems/Web programs/APP software, etc.The purpose of penetration testing services is to fully explore and expose system weaknesses so that managers understand the threats their systems face.View now -
 Kunlun China Unicom Security Assessment ServiceKunlun China Unicom's security assessment service is for professional security personnel to conduct a comprehensive security risk investigation on the application system, analyze the security problems existing in the business from a technical perspective, and guide the business side to carry out reinforcement/repair. Help you quickly locate security needs and reduce security risks.View now
Kunlun China Unicom Security Assessment ServiceKunlun China Unicom's security assessment service is for professional security personnel to conduct a comprehensive security risk investigation on the application system, analyze the security problems existing in the business from a technical perspective, and guide the business side to carry out reinforcement/repair. Help you quickly locate security needs and reduce security risks.View now -
 Geotrust DV SSL CertificateRapidSSL certificates can ensure secure information transmission between your website and your customers, enhance customer transaction confidence, facilitate transaction success, and provide users with excellent and impeccable access protection and fraud prevention from browser to server.View now
Geotrust DV SSL CertificateRapidSSL certificates can ensure secure information transmission between your website and your customers, enhance customer transaction confidence, facilitate transaction success, and provide users with excellent and impeccable access protection and fraud prevention from browser to server.View now -
 Kunlun China Unicom IT data full life cycle management solutionThe arrival of the era of data technology has made data the driving force of the future. Kunlun China Unicom can provide data visibility, information privacy compliance, comprehensive data protection, business continuity, hybrid cloud management and data life cycle management to help enterprises digitally transform and prevent ransomware attacks.View now
Kunlun China Unicom IT data full life cycle management solutionThe arrival of the era of data technology has made data the driving force of the future. Kunlun China Unicom can provide data visibility, information privacy compliance, comprehensive data protection, business continuity, hybrid cloud management and data life cycle management to help enterprises digitally transform and prevent ransomware attacks.View now -
 System security hardeningDevelop corresponding system reinforcement plans, targeting different target systems by applying patches, modifying security configurations, adding security mechanisms, system security reinforcement, database reinforcement, middleware reinforcement, and emergency configuration reinforcementView now
System security hardeningDevelop corresponding system reinforcement plans, targeting different target systems by applying patches, modifying security configurations, adding security mechanisms, system security reinforcement, database reinforcement, middleware reinforcement, and emergency configuration reinforcementView now
