- Green versionView
- Green versionView
- Green versionView
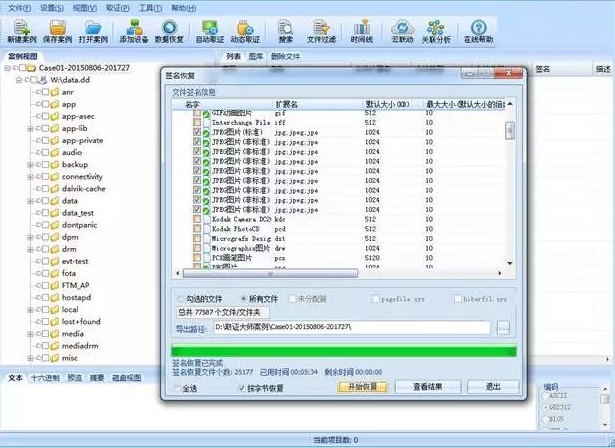
Forensics Master Software Introduction
Meiya Forensic Master is the most professional forensic software for Android phones in China. Needless to say, the actual effect and efficiency of its forensics. The editor here brings you the latest Forensics Master Professional Edition, which includes detailed operation and use procedures. Professional forensics is the Forensics Master!
Forensics Master Mobile Forensics Source
In the process of mobile phone evidence collection, the first step is to obtain electronic evidence with clue value from various relevant evidence sources on the mobile phone. The SIM card, memory, external memory card and mobile network operator's business database of the mobile phone together constitute an important source of evidence in mobile phone forensics.
1.Mobile network operator
Mobile network operators’ call data record databases and user registration information databases store a large amount of potential evidence. A piece of record information in the call data record database includes the mobile phone number of the calling/called user, the IMEI number of the calling/called mobile phone, the call duration, the service type, and the originating and terminating network service base station information during the call. In addition, the user registration information database can also obtain information including the user's name, ID number, address, mobile phone number, SIM card number and its PIN and PUK, IMSI number and service type opened. In the environment where my country is about to implement a "mobile phone real-name system", this information can play a huge substantive role in the investigation and evidence collection of future cases.
2.SIM card
In the mobile communication network, the mobile phone and the SIM card together constitute the mobile communication terminal equipment. The SIM (SubscribeIdentityModule) card is the customer identification module, which is also called the user identity card. The mobile communication network uses this card to authenticate the user's identity and at the same time encrypt the user's voice information during calls. Currently, common SIM card storage capacities include 8kB, 16kB, 32kB and 64kB. From the content point of view, the data information stored in the SIM card can be roughly divided into five categories:
(1) Original product data stored by the SIM card manufacturer.
(2) The inherent information stored in the mobile phone mainly includes various authentication and encryption information, GSIM IMSI code, CDMA MIN code, IMSI authentication algorithm, and encryption key generation algorithm.
(3) Personal data stored during the use of the mobile phone, such as short messages, phone book, schedule and call history information.
(4) Mobile network data includes network services and user information data that are automatically stored and updated by users during the use of the SIM card, such as the set periodic location update interval and the location identification number of the mobile phone at the time of the latest location registration.
(5) Other relevant mobile phone parameters, including personal identification number
(PIN), and personal unlocking number (PUK) for unlocking and other information.
3. Internal/external memory card of mobile phone
With the enhancement of mobile phone functions, the capacity of memory chips built into mobile phones has shown a trend of continuous expansion. According to the difference of stored data in mobile phone memory
It can be divided into two parts: dynamic storage area and static storage area (see Figure 1). The dynamic storage area mainly stores temporary data generated when executing operating system instructions and user application programs, while the static storage area stores the operating system, various configuration data, and some user personal data.
From the perspective of mobile phone investigation and evidence collection, the data in the static storage area often has greater evidentiary value. GSIM mobile phone identification number IMEI, CDMA mobile phone identification number ESN, phone book information, sent, received and edited short messages, calling/called call records, mobile phone ringtones, date and time, network settings and other data can be obtained in this storage area. However, in different mobile phones and mobile networks, the reading methods and content formats of these data will be different. In addition, in order to meet people's personalized needs for mobile phone functions, many brands and models of mobile phones provide external memory cards to expand storage capacity. Common external memory cards currently on the market include SD, MiniSD and MemoryStick. External memory cards are an important source of evidence when dealing with cases involving copyright or authorship.
Forensics master evidence collection process
Step 1: Preparation
First, download a picture in ".jpg" format from Baidu and copy it to the root directory of the phone's built-in storage space. The file name is "meiya.jpg", as shown in Figure 1.
Send a text message on your mobile phone to the number "1234567890" (of course, this number does not exist), the content is "Mobile Forensics", as shown in Figure 2.

Step 2: Delete relevant information
Delete the picture "meiya.jpg" shown in Figure 1 in the mobile phone file manager; delete the text message just sent on the phone, as shown in Figure 3.
Step 3: Use mobile assistant to get text messages
Connect the phone to the computer and use Xiaomi Mobile Assistant and 91 Mobile Assistant to view and export text messages. The text message just deleted was not found.
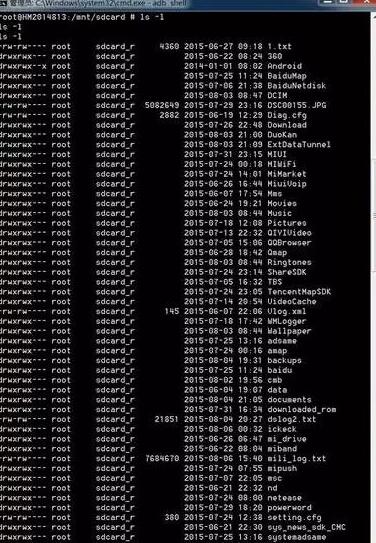
Step 4: Use ADB Shell to view files
Install adb.exe on your computer ("adb" is "Android Debug" "bridge" (most mobile assistants come with adb.exe installed), switch the working directory to the directory where adb.exe is located in the command prompt, enter "adb shell" to enter ADB Shell mode, then enter "su" to obtain Root permissions, enter "cd /mnt/sdcard" to switch the current working path to the root directory of the phone's built-in storage space, enter "ls -l" to view the detailed file/folder list, the picture "meiya.jpg" just deleted was not found. As shown in Figure 4.
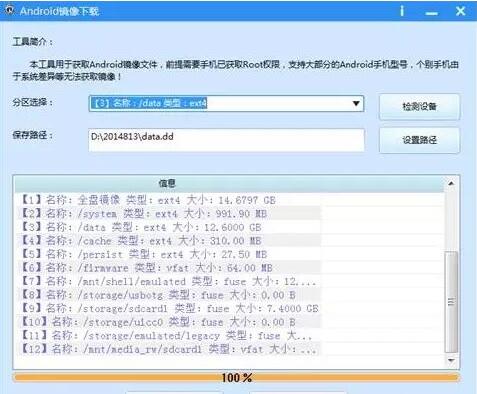
Step 5: Get the phone image
Use the "Android Image Download" tool in the "Toolbox" of the DC-4500 mobile phone forensic system to obtain the dd image of the "/data" partition of the mobile phone, as shown in Figure 5.
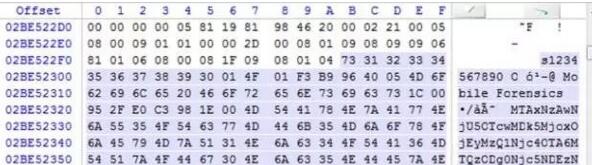
Step 6: Analyze the image
Use winhex to open the dd image you just created, and find the content shown in Figure 6 near its offset 02BE522FB. We can see the content of the text message just sent "Mobile Forensics", and found the sent number 1234567890 nearby, and also found a string of numbers "11*****39" nearby, which is the Xiaomi account used to log in to this phone.
Next, the content shown in Figure 7 was also found in the image file offset 005CCFFF0 attachment. Based on experience, there is the file header of the ".jpg" format image. Continuing to look down, we also found the end mark of the ".jpg" format file. Save the content in between as an "unnamed" file, and use "Windows Photo Viewer" to open it smoothly, as shown in Figure 8.
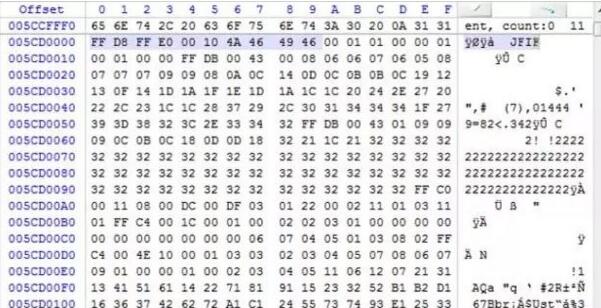

Forensic Master Result Analysis
Step 3 represents logic extraction. Various mobile phone assistants can perform basic logic extraction. This logic extraction uses the API of the Android system to read text messages, but the system does not have an API to obtain deleted text messages, so logical extraction cannot obtain deleted text messages. In fact, logic extraction can also back up relevant data through backup and then analyze it. For example, Meiya Pico's mobile phone forensics products DC4501, FL-900, etc. can extract some deleted text messages and other contents from the backup files of Android phones.
Step 4 represents logical browsing. It is also easy to understand that "meiya.jpg" cannot be seen in ADB Shell, because the image has been deleted, ADB Only files that the file system thinks exist can be displayed in the shell. After a file is deleted, the file system thinks that the file no longer exists.
Steps 5 and 6 represent physical acquisition. The image obtained in the running system in the above example is not actually a real "physical image". A more thorough physical image is obtained through Chip Off (removing the chip) and other offline methods to obtain the image. Physical mirroring is the most comprehensive method and has the best effect in forensics. The reason why it can be restored after deletion on the mobile phone is because the original content has not been overwritten. As long as the original data is still there, it can be restored. This is like having some chapters erased from the table of contents of a book. If you only look at the table of contents, you will think that these chapters do not exist. However, as long as the specific content of these chapters has not been erased, you will be able to find them page by page.
At present, the Android system does not fully encrypt storage devices. As long as you obtain the physical image and then use a hexadecimal editor to view it, you can find many clues. Of course, viewing in this way requires a lot of knowledge and rich experience in common file signatures, encodings, etc., and is often not efficient. When encountering some files that have been partially damaged, file engraving knowledge may also be required. You can use some automated tools, such as the open source scalpel.
The partition in the Android system is generally the Ext4 file system, and data recovery can be easily performed using the corresponding data recovery software. For example, in this example, the Forensic Master electronic data analysis system was used to load the dd image, and 25177 pictures were recovered using signature recovery, including the one deleted in the example. As shown in Figure 9 and Figure 10.
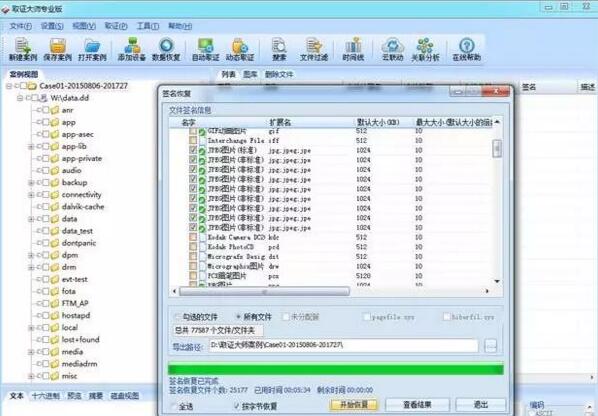

At present, most mobile phones connect to computers to view and manage files on the phone through MTP mode instead of USB flash drive mode. The advantage of this is that there is no need to consider the file system format in the phone, and it will not cause some programs in the phone that rely on the sdcard partition to run abnormally because the computer monopolizes the phone's storage space. The MTP mode is above the file system layer, and data recovery cannot be performed in the MTP connection mode. Making physical mirrors does not have this concern.
In addition, when the mobile phone is running, system operation, program operation, and user operations will cause continuous changes to the data in the mobile phone. From the perspective of keeping the inspection data as original as possible, making mobile phone images is the best choice.
Forensic Master update log
1.Fix some bugs
2. Optimized some functions
Huajun editor recommends:
The editor has been using software like Forensic Master for many years, but this software is still the best.Leyi integrated ceiling design software,Log volume calculator,Guangdong Provincial Enterprise Income Tax Declaration System,Pyle Glass Optimization Software,Taiyou CPK calculation toolIt is also a good software and is recommended for students to download and use.





































Useful
Useful
Useful