Network security level protection 2.0 construction consulting and rectification services
In order to help corporate users quickly meet the compliance requirements of Class A guarantee, our professional security team provides you with one-stop Class A guarantee consulting services, Class A guarantee evaluation, risk assessment, and safety management to help you pass the Class A guarantee quickly and worry-free. regulation. According to the relevant requirements of national information security level protection, by analyzing the actual security needs of the system, combined with the actual characteristics of its business information, and based on and referring to relevant policies and standards, a security assurance system plan is designed.
- Asset analysis, risk analysis, gap assessment, rectification and reinforcement guidance, grading consultation, filing assistance, and passing evaluation.
1. Design ideas for constructing safety genes
Compliance requirements are combined with business risk analysis. Information security risk analysis is a method of identifying security threats and system vulnerabilities faced by information systems. Through risk analysis methods, we can comprehensively grasp the full picture of security risks faced by information systems and determine information based on security risk levels. The focus of safety construction is to complete asset-based risk analysis On the basis of the actual investigation of the current status of the information system, grasp the actual gap between the current status of system protection and the baseline requirements of level protection, and conduct a comprehensive assessment of the assets, vulnerabilities, threats and business risks of the information system based on the information security risk assessment method. Conduct systematic assessment and analysis to discover business-based security risk issues. Fully combine and refine the gap analysis results and risk assessment results to comprehensively form construction needs that can meet the requirements of graded protection construction and fully guarantee business security.
2. Design ideas of defense in depth
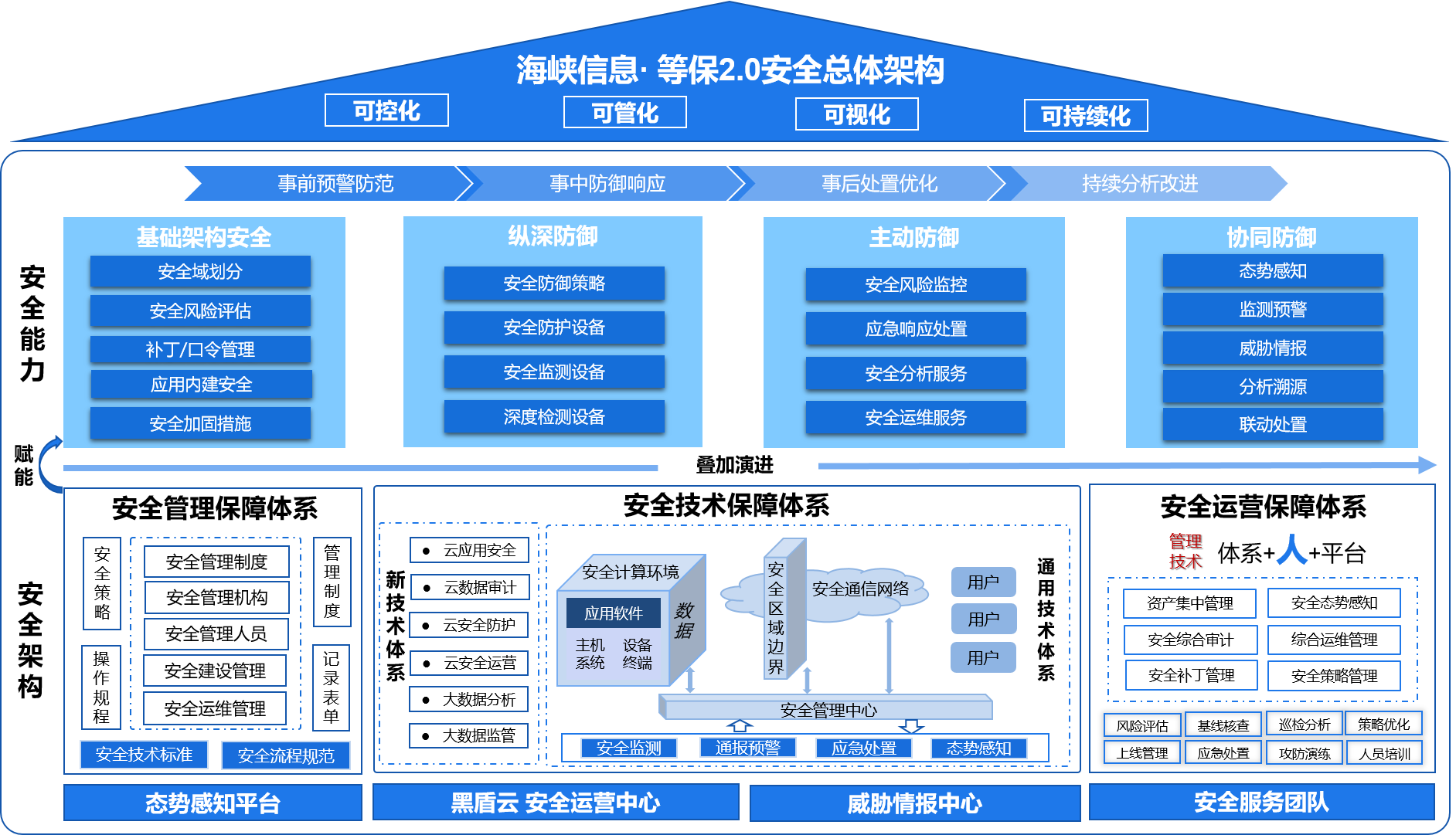
The idea of building an information system security system is to build a defense-in-depth system for information system security level protection based on the principle of partitioned and zonal protection and the idea of hierarchical defense in depth.
According to the business processing process of the information system, the system is divided into three parts: secure computing environment, secure area boundary and secure communication network. These three parts are protected based on the computing nodes, forming a computing environment security and area boundary supported by the security management center. The "one center, triple protection" structure consists of security and communication network security.
3. Design ideas for continuous guarantee and improvement
Combining security protection measures, security management systems, and security operation and maintenance services, we achieve multi-layered protection of information systems and the goals of continuous protection and improvement.
4. Design ideas for monitoring, early warning and active defense
Based on continuous risk monitoring and early warning, tracking and tracing, and joint disposal, combined with the collection of threat intelligence and security situation awareness, we can achieve the goal of active defense of network security.
Consult and plan the business system structure through our professional security service project team. Ensure that the information system meets the level protection requirements, and ultimately obtain a national network security level protection evaluation report.
All users
Product pricing
Product price = ordering interval quantity 1 * interval specification unit price 1 + ordering interval quantity 2 * interval specification unit price 2.
For example: the call rate is 0.3 yuan/minute for the part that does not exceed 3 minutes, and 0.2 yuan/minute for the part that exceeds 3 minutes; if the user calls for 8 minutes, the fee charged is 3*0.3+5*0.2=1.9 yuan.
Product price = order quantity * unit price of the range to which the quantity belongs.
For example: the call rate is 0.3 yuan/minute for no more than 3 minutes, and 0.2 yuan/minute if it exceeds 3 minutes; if the user calls for 2 minutes, the fee charged is 2*0.3=0.6 yuan; if the user calls for 8 minutes, the fee charged The cost is 8*0.2=1.6 yuan.
Product price = order quantity * unit price.
The product price is the price displayed on the page.
After-sales service time: 5*8 hours After-sales service content: Class guarantee consulting, Class guarantee construction, security consulting, security planning, risk assessment, penetration testing, security code audit, security inspection, security reinforcement, etc. Service hotline: 15259115672, 18950491560, 0591-87303715 Service email: jianggx@heidun.net
By ordering this product you agree toGoods and Services Agreement》


