Speaking of the game Public Enemy, I believe everyone is familiar with it. Do you know how to play Public Enemy Chapter 2 in the game? Below, the author brings you a gameplay guide for Public Enemy Chapter 2. If you are interested Friends can come and have a look.
Click on the mailbox and click on the document collection provided by the system. As usual, enter Tom's name in the browser, find TB at the bottom, click on the common name and TB number to collect, enter the relevant information to get the password, log in to the mailbox and click on the video, 033-8594-685, So should we meet, Elsie collects, then find and click on the collection of I am a man who does not know how to be romantic in the sent email.
Open the browser and enter the name of the heroine and find TB at the bottom to enter. Click on the common name and TB number to collect. Some of the pictures here are encrypted and will be answered later. Click here and I mean you and Adam. Edwards? Collect, then open the database and enter the relevant information of the heroine to get the specific information, then enter the information to get the password, click HK to log in, click the first sentence in the second chat, click the first sentence and the picture below in the fourth chat , I don’t want to talk to others when chatting with my sister, the first sentence in chatting with my boyfriend and the first sentence under the picture, Let’s break up, are collected.
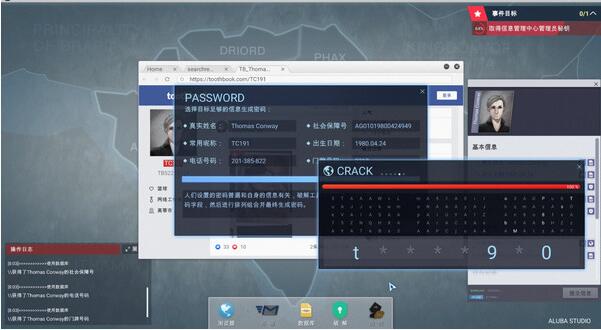
Open TB and log in to the heroine's account. At this time, you can see the previously encrypted content. Click on the injured picture and Sunflower Hotel collection. Open the database and enter the name of the third person to get specific information. Open the browser and enter the name of the third person and click For the TB content below, click on the common name and TB number to collect, then enter the relevant information to get the password, log in to the third person's account in HK, but there is nothing to collect, you can read it or not.
Open the invasion, click on the fourth singing picture to create a phishing link, enter the phone number of the heroine, drag to unlock, the album password is the idol's name, the diary clue is the rainbow in the album and my most important thing, the connections are arranged according to the colors of the rainbow, After opening the diary, click to collect the man in the seventh document and Adam in the last document, and click on the browser to collect the first sentence.
Enter Sunflower Hotel in the browser, open the website, click on the name of the hotel manager, reservation phone number, hotel picture collection, remember the first review, you will need it later. Enter the name of the hotel manager in the browser, open the TB webpage at the bottom, click on the common name, TB number, collect driving pictures, remember this tattoo picture, and click on a comment under the tattoo picture to collect.
Start the first inference, the first step is the tattoo picture, Adam, and Tom; the second step is the tattoo threater, lover Adam, and Tom are strangers; the third step is meeting in Jon's TB; the fourth step Choose the middle three; the fifth is Tom.
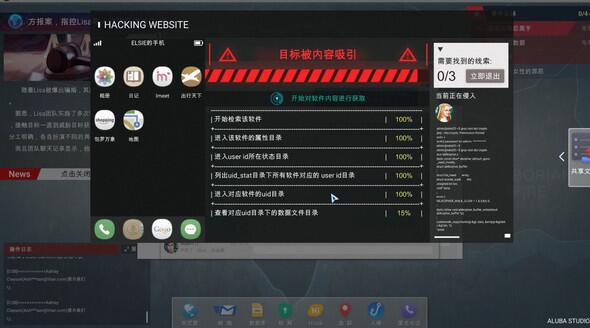
Call Sunflower customer service, the steps are Darlene Perry-October 11th, the information here is from the hotel review above, and then click on the phone number to collect. Open the database and enter the hotel manager information to query, then unlock the password and log in to the TB account. Ignore the first email for now. Click on the first sentence in the third email in the inbox, the picture in the fifth email, and you You can call me van, and collect the first sentence of the first email sent.
Click to track, it is very simple to click on similar pictures to know that the hotel manager has been promoted. Click on the eavesdropping record to see if there are no collection elements; open HK to log in to the hotel manager's account, click on the fourth sentence in the second conversation, and click on the little treasure collection in the conversation with Sarah. Open the penultimate address link of the hotel manager's information, click on the bar owner's name and HK number in the first bar rules, and click on the video and picture collection in the second bar.
Open the browser and enter the name of the bar owner to get the real name, open the database and enter the information to get some information and unlock the password, log in to the HK account, click to register an ID in the conversation with Adam, and more than 20 hotels in the last conversation, There are more than a dozen drama clubs, medicines are purchased, and triangle pictures are collected.
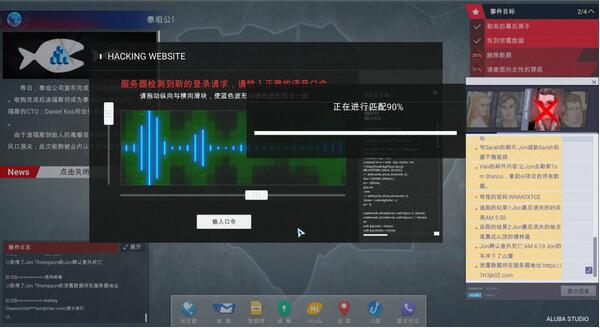
For the second reasoning, the answers are: van, AI project, Porn Collect the URL in the file, then open the intrusion, enter the obtained URL, fill in the dynamic code randomly, and adjust the sound wave yourself. After successful matching, click on the picture in the up file, and the name in the clearing plan is the name of the hotel manager. Enter the Miranda collection .
You can successfully pass the level after choosing to submit a bunch of information.
The above is the gameplay guide for the second chapter of Public Enemy on the Internet brought by the author. I hope it can help everyone pass the level smoothly.




